
picture manipulation incident of O.J. Simpson mugshot
by Nurul Shabilla Shaherra Binti Muhammad Asri Tan CD17058
Discussion based on Case Study II:
a) Being an investigator, you should think like a criminal. Take note that the perpetrator may say his accounts are being hacked or used by others during the defense. Identify some convincing digital evidence related to the case that should you get to prove that he is the one sharing the manipulated or edited pictures on the social media platform.
There are four phases involved in the initial handling of digital evidence: identification, collection, acquisition, and preservation
in the identification phase, the investigator seek to answer such as Who was involved?, What happeneed?, When did the cybercrime occur?, Where did the cybercrime occur? and How did the cybercrime occur?.
The collecting methods differ based on the type of digital technology and the public and private infrastructure where digital evidence is stored (e.g., computers, mobile, social media, and cloud; see the Scientific Working Group on Digital Evidence ( SWGDE ) for various digital forensics practises relating to multimedia, film, and mobile).
The entire acquisition process should be documented. This documentation should include detailed information about the digital devices from which evidence was extracted, the hardware and software used to acquire the evidence, the manner in which the evidence was acquired.

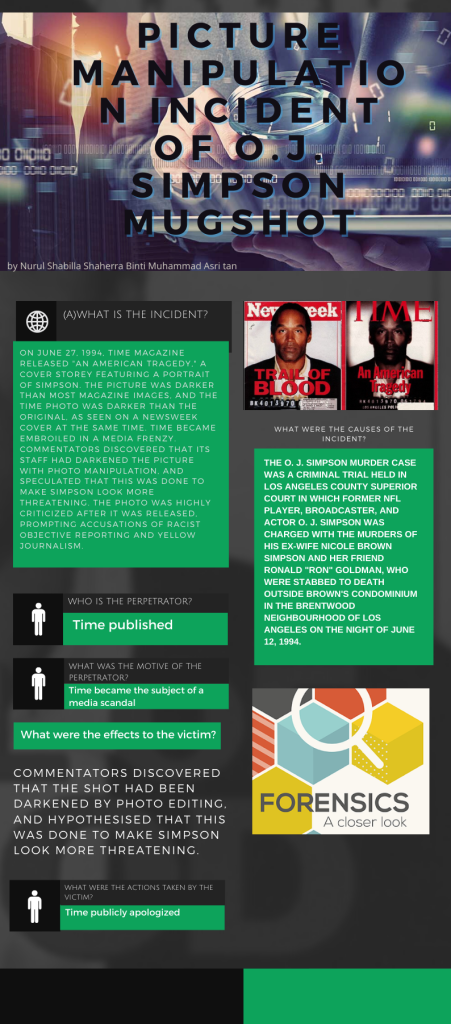
The image was darker than a typical magazine image, and the Time photo was darker than the original, as shown on a Newsweek cover released at the same time.
b) This is a practical question. Let say you are the assigned forensics analyst for this case. Present step by step how to prove the pictures in the case study are not original by providing steps by steps.
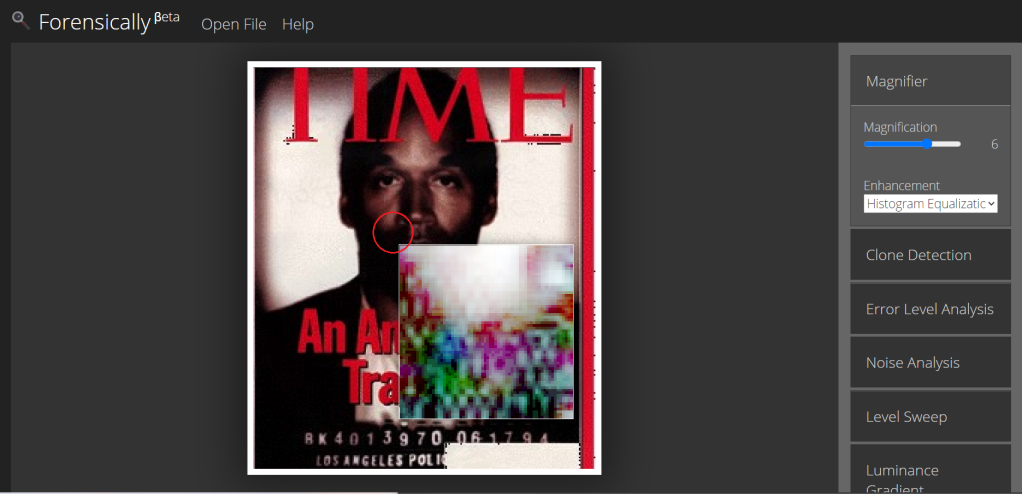
First, Use “Forensically” to compares the original image to a recompressed version. This will draw attention to manipulated areas in a variety of ways. They may be darker or lighter, for example, than identical regions that have not been manipulated.
Error Level Analysis

Magnifier
c) All social media companies are located outside Malaysia. Plan how you should liaise with the company to seize the evidence and stop the attack.
Every precaution must be taken in the collection, preservation, and transportation of digital evidence. First responders should follow guidelines to ensure the proper handling of digital evidence at an electronic crime scene
At the scene, identify, locate, seize, and secure all digital evidence. Pagers, mobile phones, iPods, iPads, laptop (notebook) computers, PCs, displays, and auxiliary equipment such as mouse, keyboard, external hard drives, disc drives, hand-held GPS devices, printers, and external power supplies will all fall into this category.
Reflection
Artifacts
1, F., 29, J., & 26, J. (2020, October 13). Photo Forensics: Detect Photoshop Manipulation with Error Level Analysis. Infosec Resources. https://resources.infosecinstitute.com/topic/error-level-analysis-detect-image-manipulation/.
HEADT Centre – How to Detect Image Manipulations? Part 1. (n.d.). https://headt.eu/How-to-Detect-Image-Manipulations-Part-1.
Wikimedia Foundation. (2021, May 15). O. J. Simpson murder case. Wikipedia. https://en.wikipedia.org/wiki/O._J._Simpson_murder_case#Media_coverage.